With advancements in technology and the demand for effective security systems on the rise, face detection locks have increasingly gained popularity in recent years. This technology, although relatively new, has shown immense promise in providing secure authentication for a wide array of applications. This piece delves into the efficiency of these biometric systems, focusing on how they could potentially shape the future of security.
An impressive characteristic of face detection lock systems lies in their ability to accurately identify individuals based on unique facial features. Countless people worldwide are now straying from traditional alphanumeric passcodes and fingerprint scanning, placing their trust in this revolutionary technology. But how effective are these facial recognition locks? This is a question that must be answered, taking into consideration specific factors such as speed, accuracy, ease of usage, among other things.
To truly assess the efficiency of facial recognition locks, it’s crucial to understand their workings. Rooted deeply in complex technological mechanics, these systems employ artificial intelligence and machine learning to identify human faces. Utilizing intricate algorithms, these locks scan, store, and compare facial features, providing an additional layer of security. However, it’s essential to weigh the benefits and downsides of such systems in equal measure.
In this piece, we will examine how facial recognition locks can redefine security mechanisms, contemplate their benefits and potential drawbacks, and predict their impact on future technological trends.
From Classic Keys to Advanced Face ID: The Security Transformation
The realm of security has undergone a tremendous change over the years. It started from simple physical keys and has now evolved into sophisticated facial recognition systems. Unlocking the potential future of safety measures, the modern face id system is ironically inspired by the age-old concept of recognizing individuals by their facial features.
Security in the Early Days
In the early days, security was purely physical. It involved the use of metal keys and mechanical locks. The higher the complexity of the lock, the higher was its perceived level of security. However, these systems had several drawbacks. They could easily be picked, duplicated, lost, or stolen. Furthermore, if a key was lost, changing the entire locking system was often necessary to maintain security.
The Advent of Digital Security
As technology progressed, so did the methods of security. The era of digital security began with the advent of password and pin-based systems. These improved the drawbacks of traditional methods, as there was nothing physical to lose or steal. However, they brought with them a new set of challenges. Remembering complex passwords could be tough, and there was, of course, the ever-present risk of these passwords being hacked.
Beyond Passwords: Facial Recognition Security
Then came the era of biometric security. Instead of relying on something the users have (like a key or a password), these systems began relying on who the users are. Fingerprint scanners became a common feature in many devices, paving the way for the development and incorporation of facial recognition technology.
In the face ID systems, algorithms and predictive models are employed to analyze specific features on the face. It’s efficient, personal, and incredibly hard to fake. Some systems have even incorporated 3D technology to add a deeper layer of security, making it nearly impossible to be tricked by photographs or masks.
Security has indeed come a long way from metal keys to facial recognition. From guarding our homes to protecting our digital lives, the evolution in security measures reflects the advancement in technology and our inherent need for safety. As we look towards the future, we can expect even more sophisticated and efficient forms of security to emerge.
Understanding the Mechanism of Locking Systems Powered by Facial Identification
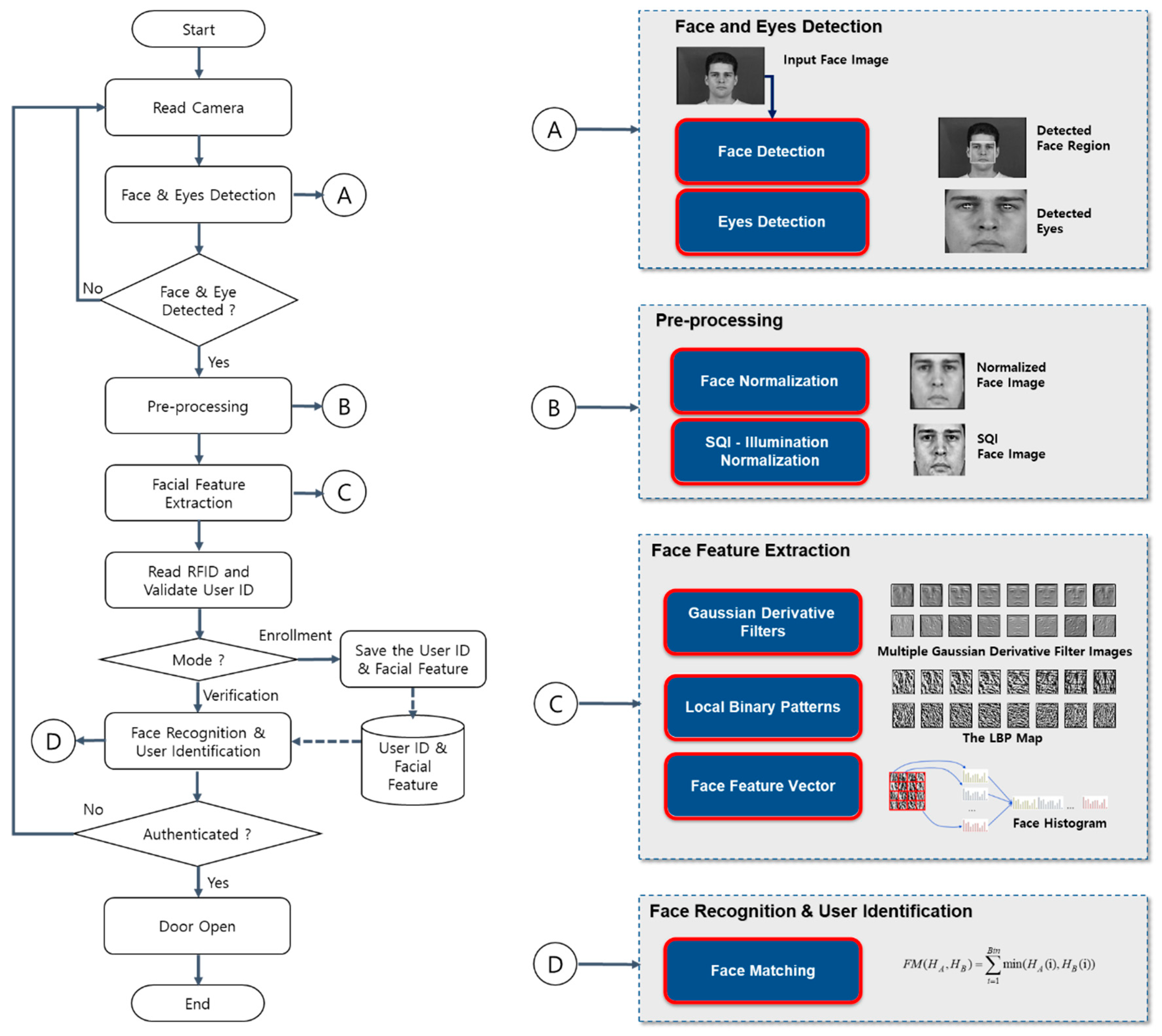
A locking system empowered by facial identification is a cutting-edge technology that leverages biometric information to enhance the security of a facility. This futuristic mechanism requires no physical key or card, rather it functions by scanning and recognising the unique characteristics of an individual’s face.
The crux of a facial identification-based locking system lies in its capability to process and memorize intricate subtleties of facial features. This involves a complex process of capturing, analysing and comparing the facial data to the pre-stored data in the locking system. The system, thus, grants access only when a match is found, ensuring a high level of security and minimizing the scope of unauthorized entry.
A few primary stages in the working of such a locking setup are:
- Image Capture: This is the initial phase where the individual’s face is digitally recorded via a camera.
- Face Recognition: Next, the system identifies the face in the image, ignoring other objects in the scenario.
- Feature Extraction: In this vital stage, the system analyses and maps distinctive features of the face, such as the distance between the eyes or the angle of the chin.
- Comparison and Match: The mapped data is then compared with the pre-stored dataset. If a match is detected, access is granted.
In sum, a locking mechanism powered by facial recognition is a progressive answer to evolving security needs. By embracing such technologies, we indeed step closer to unlocking a secure future.
Unlocking the Mysteries: How Does Facial Recognition Technology Work?
Facial recognition technology is an intriguing advancement that enables a computer to capture, analyze, and identify human faces. But what is the principle that drives this remarkable technology, and how does it operate to ensure efficient security through facial recognition locks?
The underlying science of face recognition technology lies in the series of processes designed to perform complex evaluations of a particular face. The technology uses biometrics to map facial features from a digital image or video. It then compares this information with a database of known faces to locate a match.
Key Steps in Facial Recognition Technology
- Face Detection: This is the initial step where the system discovers and recognizes a human face within the object or environment.
- Face Capture: In this stage, the system gathers the necessary data by capturing specific raw facial features.
- Data Conversion: This step involves converting the captured data into a format that the system can process – typically a numerical code or string.
- Face Match: Lastly, the processed data is compared with the existing database to find a match.
It’s also important to note that modern facial recognition systems use deep learning algorithms and artificial neural networks to enhance their accuracy. These systems are trained to analyze patterns in the data collected, allowing for a more sophisticated level of detail recognition, such as recognizing faces in different lighting or from different angles.
The efficiency of Facial recognition locks is heavily dependent on this technology’s ability to seamlessly integrate these processes. This ensures that the locks can correctly identify authorized users, even in varying conditions, and deny access to unauthorized individuals–providing a robust, keyless, and efficient security solution.
As the science behind facial recognition technology continues to advance and evolve, the potential applications extend far beyond security, unlocking the future of personalized experiences in digital media, marketing, and more.
The Mechanism Behind Facial Recognition Security Systems
You might wonder how facial recognition mechanisms utilized in progressive locking systems function. The principles behind their operation are quite fascinating, involving not just technology but also elements of artificial intelligence.
Let’s discuss in detail:
The Initial Setup
Initially, the facial recognition sensor requires a ‘master’ image of your face to recognize it later. This is known as face enrollment, where the system captures the details of your face from various angles to register your facial features. The software then creates a numeric representation of these features, creating a facial signature or template.
Scanning and Recognition
Once your face is registered, each time you present your face to the lock, the technology starts a complex process. The onboard camera captures an image of your face and compares it to the registered one. The software then transforms this image into a numeric representation.
The system examines the inherent features of your face – the distance between eyes, the width of the nose, the shape of cheekbones, and even the jawline – to validate your identity. Strong software also considers changes such as facial hair, glasses or age effects, to ensure accurate recognition.
Authentication and Access
The final step in facial identification involves comparing the current numeric representation with the facial signature initially registered. If there’s a sufficient match, the system authenticates the user and unlocks the security system, granting access.
- Thermal Imaging: Some advanced facial recognition locks use thermal imaging to increase accuracy. This technology reads the heat signature to form a ‘thermal faceprint’
- 3D Recognition: Other systems use 3D recognition using infrared light projection and sensors, which can prevent tricking the system with simple photographs.
The evolution of facial recognition in locking mechanisms has unraveled a new horizon in security infrastructure. There’s a continuous effort to improve accuracy, speed, adaptability, and in creating systems that can operate flawlessly under various environmental conditions.
Decoding the Precision and Effectiveness of Facial Recognition-Enabled Security Measures
Facial recognition technology has introduced a new dimension in the security landscape, with a specific focus on lock systems. The convenience of these systems, driven by the ease of use and increased security assurance, puts them at the forefront of innovative safety solutions. Nevertheless, the true hallmarks of this technology are its precision and efficiency, which warrant a deeper understanding.
Finesse and Robust Performance of Facial Recognition Locks
When we analyze the accuracy of face recognition-based lock systems, the discussion revolves around how precise these systems are in identifying authorized personals and restricting access to intruders. Like any technology relying on biometrics, these systems strive for high true positive rates (correctly identifying authorized individuals) and low false positive rates (incorrectly recognizing unauthorized individuals as authorized).
The systems use complex algorithms to analyze hundreds of facial features, creating a faceprint unique to each individual. It’s this intricacy that contributes to the high precision of face recognition locks.
In terms of efficiency, a crucial strength of facial recognition locks is their non-contact, swift operation. Opposed to traditional locks requiring physical contact and time, face recognition technology provides immediate authentication, streamlining the process of accessing secured premises.
- A one-on-one comparison mode, where the system compares the captured face with the stored faceprint of the authorized individual
- A one-to-many comparison mode, where the system compares the captured face with all the stored faceprints in the database
Both modes have their strengths. The one-on-one mode operates swiftly, while the one-to-many mode adds an additional layer of security by cross-checking the digital image with a large number of faceprints.
In conclusion, the efficiency of facial recognition security is predominantly defined by the system accuracy and the speed of its operation, contributing to a balance between robust security and user convenience.
Understanding the Advantages and Drawbacks of Biometric Facial Recognition Security Systems
Biometric facial recognition security systems have become increasingly popular in recent years. They use advanced technology to capture and compare facial features for the purpose of verification or identification, effectively functioning as locks. However, like any technology, they have their strengths and weaknesses. A comprehensive understanding of these aspects is instrumental in making an informed decision whether to employ such systems.
The Strengths of Biometric Facial Recognition Security Systems
One major benefit of these systems is their high level of accuracy. The technology analyzes multiple facial features, making it highly unlikely for two people to have identical results. This feature reduces the chances of unauthorized access. Also, these systems are extremely convenient. There is no need to remember passwords or carry extra tools or keys- a glance at the camera is all it takes to gain access.
Moreover, these systems offer increased security. They are more difficult to deceive than traditional systems, such as those relying on passwords or keys which can be easily stolen, shared or hacked. Additionally, they offer a level of contactless authentication, making them hygienic and suitable for the post-COVID era.
The Drawbacks of Biometric Facial Recognition Security Systems
Despite the aforementioned benefits, these systems are not without faults. The most notable downside is the privacy concern. In a world where privacy is increasingly coveted, the storage of facial data can be perceived as invasion of privacy. Additionally, there is always the risk of database breaches, leading to personal information falling into the wrong hands.
A prominent technical downside is the possible errors. Facial recognition technology isn’t foolproof and can struggle with accurately identifying individuals in poor lighting conditions or if the individual’s facial features have significantly changed. Additionally, if the system’s hardware or software fails, access will be lost until repairs are made, creating inconvenience and inefficiency.
Understanding the strengths and weaknesses of biometric facial recognition security systems can provide a well-rounded view of whether this innovative technology fits into one’s personal or professional security plan.
Understanding the Potential Security Vulnerabilities of Locks Utilizing Facial Recognition
While the efficiency, convenience, and futuristic appeal of face-detection based lock systems are undeniable, they do not come without certain potential vulnerabilities. Understanding these risks is crucial for anyone considering their application and depends on the accurate evaluation of the technology underpinning these systems.
Reliability of Technology
While sophisticated, this lock technology is not foolproof. Certain basic methods can be used to fool these systems. For instance, high-quality photos or 3D masks of the user’s face can be used to trick the system, essentially providing a key to anyone who can obtain such a representation of the intended user. Therefore, even in the era of advanced lock systems like facial recognition, traditional security risks like duplication and impersonation remain.
Potential Data Privacy Issues
Another key aspect is the question of data privacy. While FRLs (Facial Recognition Locks) offer heightened physical protection, they paradoxically might pose a larger virtual threat. The information these locks collect is highly personal and, if accessed by a third party, could significantly compromise a user’s privacy. Although the data is typically encrypted, the risk of breaches still exists. Additionally, unlocked data could potentially be used to create deep fakes, contributing to an increasing online threat landscape.
Overall, the move towards facial recognition locks signifies exciting progress in security technology. However, it also highlights the fact that convenience and efficiency must be balanced with an understanding of their potential vulnerabilities and the proactive management of such risks. Therefore, understanding these systems involves not only embracing innovative possibilities but also acknowledging and addressing their pitfalls.
Addressing Privacy Issues Concerning Locks Activated by Facial Characteristics
Advancements in technology have resulted in the development of automated security systems that employ the use of biometric data. Among the biometric options available, facial recognition activated security systems have gained substantial popularity. These mechanisms, while efficient, have aroused significant privacy concerns.
Identifying the Concerns
The application of a facial recognition locking system involves the collection, storage, and processing of personal facial data. This process could intrude upon an individual’s personal space, leading to questions regarding the confidentiality, integrity and security of the data, and issues around consent to data capture and manipulation. Risks inherent to these concerns include unlawful access, data theft, and potential misuse of the acquired data.
Moreover, aspects such as race, gender, and age, can be extracted from facial data. This could result in discriminatory practices if the information falls into the wrong hands.
Tackling Privacy Issues
Prioritizing privacy protection, tech companies and security system manufacturers must take a proactive stance. Below are some steps that they can undertake:
- Ensuring data security: Establishing strong encryption protocols can prevent unauthorized access and protect data integrity.
- Seeking explicit consent: Users must be fully informed about the data collected, the purposes, and the manner of its use. Their explicit consent should be sought before data is captured.
- Implementation of Privacy by Design: Systems should be designed with privacy as a fundamental feature, not an afterthought. This can be incorporated through the use of data minimization techniques and anonymization where possible.
- Regular audits and transparency: Regular system reviews and audits help maintain and improve security. Providing transparency reports can also help gain user trust.
To conclude, while facial recognition locks can offer an impressive level of security, it is vital to address the accompanying privacy concerns effectively. By doing so, we can ensure that these innovative technologies serve their purpose without infrac
Practical Applications of Face Recognition Access Control
The Innovative Use of Facial Recognition Technology in Premises Access Control: Some Successful Cases
Facial recognition lock systems are at the forefront of secure access control innovations. They unlock a secure future by leveraging the potential and efficiency of this technology. Several organizations and locales around the globe have successfully implemented this technology, proving its merit and benefits.
One such example is the utilization of facial recognition security systems in some major airports. Travel security is of critical importance, and advanced facial recognition technology plays an integral role in enhancing this security. The system is set up to recognize facial patterns and features, ensuring an additional layer of security in the authentication process. The usage of this technology has resulted in smoother boarding processes and reduced identity fraud incidents.
Amazon Go stores are another notable case. These cashier-less retail stores utilize facial recognition systems to offer a unique shopping experience. Customers walk into a store, pick up their desired items, and simply walk out; the system recognizes the shoppers and deducts the cost from their Amazon account. This frictionless shopping experience allows for maximum convenience and security.
Banks have also started to incorporate facial recognition technology for both internal and external applications. It is used for restricting access to secured areas, similar to how it is used for home security. On the customer front, facial recognition serves the dual purpose of reducing fraud and enhancing customer experience. Customers can now conduct transactions at ATMs and access their account information with more ease and security.
Facial recognition technology has also found its way into smart home systems. Homeowners can now regulate access to their homes with this technology, reducing the risk of unauthorized intrusion.
- Facial recognition in airports has resulted in smoother on-boarding and reduced fraud.
- Amazon Go stores use facial recognition to make shopping as effortless as possible.
- Banks use facial recognition to enhance security and customer experience.
- Smart home systems utilize facial recognition for enhanced home security.
These examples barely scratch the surface of the potential applications of facial recognition locks. As technology advances, the efficiency and ubiquity of these systems are expected to grow. The future looks secure with facial recognition technology.
Future Projections: The Position of Facial Recognition in Advanced Security Systems
Observing future trends in digital safety protocols, facial recognition technology’s role is escalating exponentially. The face scan lock method has become the centerpiece of modern security systems due to its incredibly high efficiency. Let’s explore why facial recognition is paving the path towards the next generation of advanced security solutions.
1. High-level Accuracy and Efficiency
Security systems that use face-mapping technologies have significantly improved identification accuracy, almost eliminating the possibility of error. Not only does this hyper-accurate mechanism add a more profound layer of protection and access control, but it also offers an easy and effortless authentication process.
2. Incorporation in Consumer Electronics
Consumer electronics manufacturers are increasingly integrating biometric recognition technology into their devices. From smartphones, smart home devices, to vehicles, facial recognition adds an extra, user-friendly layer of security that’s hard to compromise.
3. Scalability and Versatility
Beyond the personal use spectrum, advanced facial recognition techniques offer both scalability and versatility. They have extended applications in public security systems, such as surveillance, and crowd or event management.
- Surveillance: Advanced facial recognition technologies allow law enforcement to swiftly recognize and track individuals in real-time during investigations.
- Crowd Management: Large gatherings can benefit from such systems, which help maintain safety protocols by identifying unauthorized, missing, or suspicious individuals.
- Events: Face scan locks ensure that only approved individuals can access certain areas during large-scale events.
In conclusion, the future of security systems largely rests on the shoulders of facial recognition technology. Its efficiency, ease-of-use, accuracy, and versatility make it an indispensable tool for next-generation security protocols.
Selecting the Suitable Facial Recognition Security System for Your Requirements
As we step into the future, the importance of digital security measures such as facial recognition technology becomes increasingly clear. However, choosing the right facial recognition lock to fulfill your specific needs can be a tricky endeavor. Here are some guidelines to steer you in the right direction.
Firstly, the level of security required must be ascertained. High security areas such as homes, offices or confidential data rooms would require a facial recognition lock that can perform deep learning analysis, cross-referencing facial structures to a detailed and thorough algorithm. Meanwhile, low-security areas such as a personal bag or box may simply require a basic facial recognition system.
Factors to Consider When Selecting a Facial Recognition Lock
- Guaranteed Accuracy: A high-performing system must be highly reliable and accurate, decreasing the chance of false acceptance or rejection.
- Scalability: The system should be flexible enough to manage a wide range of users while maintaining its efficiency. This becomes extremely important for areas with high foot-traffic such as offices.
- User-friendliness: The ease of use is crucial in ensuring all potential users are comfortable with the system, otherwise, it will fail to accomplish its purpose.
Lastly, the cost of the system will inevitably play a role in your decision. Higher performance recognition locks are often more expensive than their basic counterparts. It is important to strike a balance between the security requirements and budget constraints. So why not unlock your future by making an educated and informed decision on your next facial recognition lock?
FAQ: Facial recognition locks
What is a facial recognition lock?
A facial recognition lock is a type of security system that uses biometric technology to grant or deny access based on facial features. It can be used on devices like smartphones, tablets, and door security systems.
What features should I look for in a facial recognition lock?
When choosing a facial recognition lock, consider its accuracy and speed of recognition. Also, check if it has a liveness detection feature to prevent the use of photos or masks. Its storage capacity for face templates and compatibility with your device or system are also vital features.
Can facial recognition locks work in low light conditions?
Yes, but this depends on the model. Some advanced facial recognition locks use infrared technology and therefore are capable of recognizing faces even in the dark. However, their effectiveness can vary, and it’s recommended to check this feature before purchase.
How secure are facial recognition locks?
Facial recognition locks are generally secure as they use unique biological traits for identification. However, the level of security may vary depending on the recognition technology used. Advanced systems which combine facial recognition with other biometric data, like iris or fingerprint scans, tend to be more secure.
Are facial recognition locks easy to install?
Facial recognition locks’ installation complexity can vary depending on the make and model. Some locks are simple to install and come with user-friendly manuals, while others might require professional installation. It is advisable to check the installation instructions before purchasing.